This report was written by Tiger Research, analyzing the asset and custodian layers of BTCFi, examining how wrapped Bitcoin tokens bridge Bitcoin into DeFi through various custody models and their associated trade-offs between security, trust, and usability.
TL;DR
Wrapped BTC as the gateway to BTCFi: Wrapped BTC tokens bridge Bitcoin into DeFi by locking BTC in custody and issuing equivalent tokens on programmable chains, balancing security with usability.
Custodian layer = trust model: The core risk lies in "who holds the keys," with custody models ranging from centralized institutions to decentralized cryptographic protocols, each trading off efficiency, transparency, and counterparty risk.
Fragmentation & the path to standardization: Unlike stablecoins, wrapped BTC lacks a universal standard with liquidity split across multiple tokens, limiting composability and requiring market consolidation around a few trusted wrappers to serve as Bitcoin's "USDC equivalent."
1. Wrapped BTC: The bridge between Bitcoin and DeFi
Bitcoin’s base layer is highly secure, censorship-resistant, and has proven itself over more than a decade of operation. However, it is deliberately limited in programmability: Bitcoin Script is not designed for complex smart contracts, nor does Bitcoin natively support interoperability with other blockchains.
As a result, while Bitcoin is the most valuable cryptoasset by market capitalization, much of its capital remains “idle” from the perspective of DeFi. To unlock Bitcoin’s utility in programmable environments, wrapped BTC (wBTC) was introduced as a bridge to other blockchain networks.
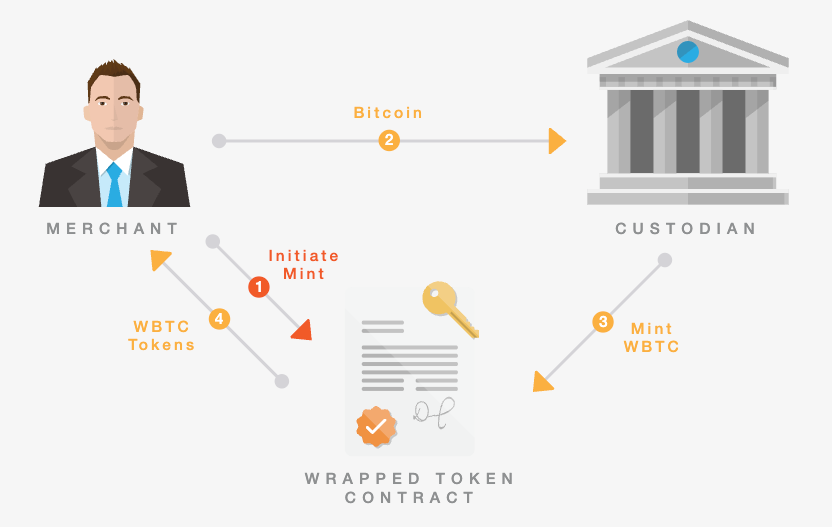
Wrapped BTC tokens are representations of Bitcoin on other programmable chains, enabling BTC to be used in smart contracts, lending protocols, and other DeFi applications. These tokens are issued when real BTC is locked in some form of custody, and an equivalent token is minted on the destination network. The custodian, whether centralized, federated, or decentralized, holds the actual BTC and guarantees redemption at a 1:1 ratio.
However, wrapped BTC is not a monolith. Different tokens vary in their custody model and functional design. Different tokens vary in their custody model and functional design.
The custody model determines the security guarantees and trust assumptions, while the token function defines the economic purpose of the wrapped asset. Together, these two dimensions provide a structured lens for analyzing the BTCFi token landscape.
1.1. Centralized Custody
In the centralized custody model, all BTC reserves are held and managed by a single regulated entity such as a trust company or major exchange. When users deposit BTC, the custodian issues an equivalent amount of wrapped BTC on the target chain. When the token is redeemed, it is burned, and the custodian releases the underlying BTC.
This model has enabled the largest-scale adoption of wrapped BTC, with WBTC($14B), cbBTC($5.6B), 21BTC($690K) collectively dominating market liquidity. Operational processes are typically fast, and institutional-grade custody frameworks, often with insurance coverage and regulatory compliance, make these tokens attractive for large-scale and institutional participants.
However, centralized custody introduces a single point of failure. The solvency, security, and operational integrity of the custodian are critical to the system’s safety. Any compromise, insolvency, or regulatory action can immediately jeopardize all reserves and halt redemptions, regardless of on-chain token liquidity.
1.2. Federated Custody
Federated custody distributes control of BTC reserves across multiple known entities, each holding part of the signing authority in a multi-signature arrangement. No single participant can unilaterally move funds, and withdrawals require a quorum of signers to approve transactions.
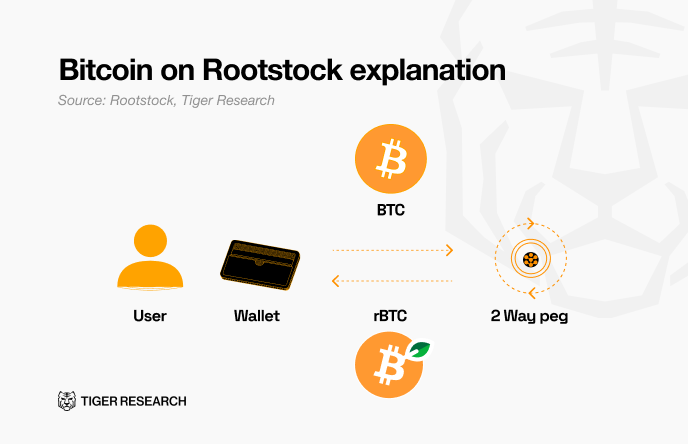
Federations are often composed of exchanges, infrastructure providers, or ecosystem stakeholders whose public identities add reputational accountability. Examples include BTC.b on Avalanche, L-BTC on Liquid, rBTC on Rootstock.
For example, rBTC on Rootstock operates through the PowPeg Federation for security. This system uses a 5-of-9 multi-signature Bitcoin wallet managed by nine institutions, including BlockVenture and eight other crypto-native organizations. Under this structure, at least five out of nine institutions must approve any transaction execution. The Federation jointly supervises the minting and burning processes of rBTC. Users can process Bitcoin deposits and withdrawals through the PowPeg bridge.
This model reduces the risk of unilateral compromise and offers operational resilience if members are geographically and organizationally diverse. The trade-off is that users must still trust the collective honesty of the federation; a collusion of a quorum can seize reserves. Peg-out times also tend to be slower due to coordination requirements, and governance processes are often opaque to end users.
1.3. Decentralized / Cryptographic Custody
Decentralized or cryptographic custody removes human discretion from reserve management, relying instead on protocol-enforced rules.
BTC is locked using Bitcoin-native scripts, threshold cryptography, or multi-party computation, with signers randomly selected from a decentralized network and bonded with collateral that can be slashed for misbehavior.
This approach eliminates reliance on specific institutional actors and maximizes censorship resistance, aligning most closely with Bitcoin’s ethos of trust minimization. Current examples include tBTC on Ethereum and Arbitrum, sBTC on Stacks, and stBTC in the Nomic/Babylon ecosystem.
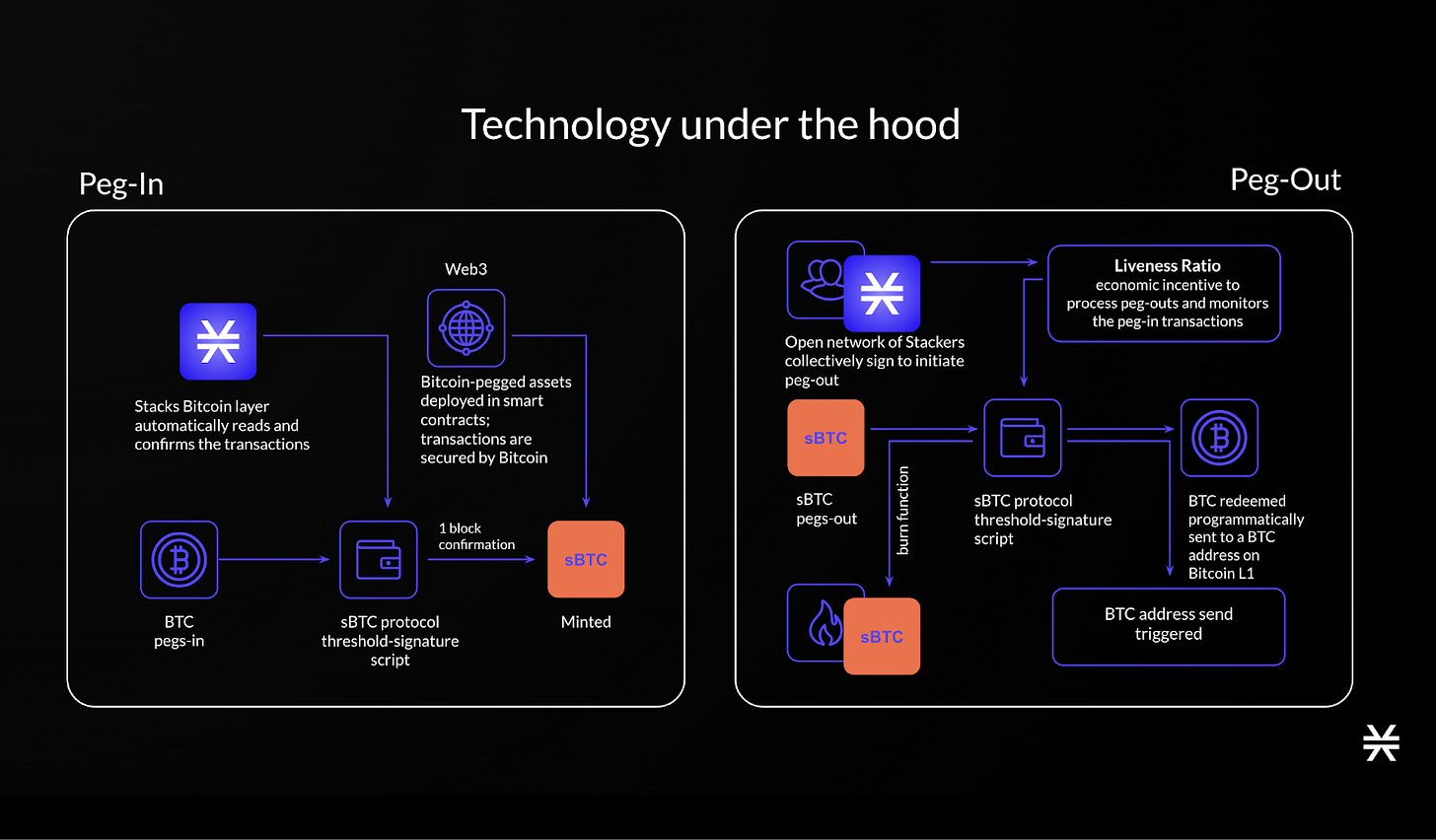
In the case of sBTC on Stacks, Bitcoin is pegged into the system by sending BTC to a threshold-signature script, which is monitored and confirmed by the Stacks Bitcoin layer. Once confirmed, an equivalent amount of sBTC is minted and can be used in smart contracts secured by Bitcoin.
For peg-outs, the process of converting wrapped Bitcoin back to original Bitcoin, an open network of "Stackers" jointly sign to convert sBTC back into native BTC.
The protocol provides economic incentives to Stackers through a liveness ratio that measures peg-out processing speed. If processing is delayed, collateral assets are partially slashed, while fast processing results in rewards. As a result, BTC is automatically sent back to user-controlled Bitcoin addresses. This design combines cryptographic custody with incentive-driven participation, aligning trust-minimization with Bitcoin's security guarantees.
While technically robust in theory, these systems are complex and introduce risks from smart contract vulnerabilities, cryptographic flaws, or poorly designed incentive structures. They also face slower adoption due to integration challenges and the operational complexity of bridging BTC in a fully decentralized manner.
2. Custodian layer: Who Holds the Keys?
At the heart of every wrapped Bitcoin token lies the custodian layer — the entity or mechanism that controls the private keys to the BTC backing the token. The security model of a BTCFi asset is, in essence, the security model of its custodian.
Broadly, custody arrangements in BTCFi can be grouped into three categories: institutional custody, retail self-custody, and shared custody models.
2.1. Institutional custodians
Institutional custodians are regulated entities that manage cryptoassets on behalf of clients under strict compliance frameworks. Prominent examples include BitGo (custodian for WBTC), Coinbase Custody (custodian for cbBTC), Fireblocks (MPC custody for enterprises). Many qualify as “Qualified Custodians” under financial regulations, offering segregated accounts, insurance coverage, and independent audits.
This model plays a central role in BTCFi adoption by providing institutional investors with a custody arrangement that meets legal and operational requirements. BitGo’s transparent proof-of-reserves and long-standing industry reputation have been critical to WBTC’s dominance in Ethereum-based DeFi. Similarly, Coinbase allows institutional clients to wrap and unwrap BTC seamlessly within their accounts, reducing operational friction.
However, institutional custody introduces counterparty risk. Users must trust that custodians will not mismanage, lose, or freeze funds. There is also regulatory risk: custodians may be compelled to halt redemptions or surrender assets under legal orders.
While institutional-grade custody is often mandatory for regulated funds and ETFs, its centralized nature runs counter to the decentralization ethos that underpins Bitcoin.
2.2. Retail self-custody
At the opposite end of the spectrum, individual Bitcoin holders often store their BTC in hardware wallets such as Ledger or Trezor. Self-custody is widely regarded as the gold standard for asset security, eliminating reliance on any third party and ensuring that users retain sole control over their private keys.
In the context of BTCFi, however, self-custody presents practical challenges. To use BTC in DeFi, holders must typically transfer their coins to a bridge, custodian, or smart contract, relinquishing control, even if temporarily. Most wrapped BTC designs require users to exit self-custody during the wrapping process.
Innovations such as Partially Signed Bitcoin Transactions (PSBTs) aim to reduce this trade-off. Nevertheless, most BTCFi participation still requires trusting either a centralized custodian or a decentralized bridge for the duration of the wrap.
Self-custody eliminates counterparty risk but also limits access to yield and other DeFi features, which deters many long-term Bitcoin holders from bridging their coins. The principle of “not your keys, not your coins” continues to shape adoption patterns, and any BTCFi model targeting retail users must offer verifiable, on-chain security guarantees comparable to those of hardware wallet storage.
2.3. Multi-signature and smart contract custody
Between institutional custody and individual self-custody lies a spectrum of shared custody models, where control is distributed across multiple parties — human or machine.
One example is federated. These rely on a group of known functionaries who collectively control BTC reserves via an M-of-N signature scheme. For instance, Liquid’s federation requires 11 of 15 members to authorize withdrawals. This reduces the risk of unilateral abuse but introduces coordination risk — if members are unavailable or in dispute, withdrawals may be delayed. Transparency also varies: while federation members may be publicly known (e.g., vetted exchanges), internal governance processes are often opaque.
User-focused multi-sig services such as Casa and Unchained Capital offer another form of distributed control. Although not used to issue wrapped BTC, these models illustrate how key management can be shared without any single party having full access. In theory, a bridge could use this structure, with reputable institutions each holding a key. WBTC itself has taken steps toward this model: BitGo recently onboarded BiT as a second co-custodian to decentralize custody further.
These designs minimize counterparty risk by encoding trust into protocol logic, though they introduce new risks around smart contract security and protocol complexity. Auditing, formal verification, and slashing mechanisms become critical to ensuring system reliability.
In summary, the custodian layer in BTCFi spans a spectrum from fully centralized institutions to fully decentralized cryptographic systems, with hybrid models in between. Each model carries its own balance of risk, efficiency, and accessibility. For BTCFi to scale, especially with institutional capital, it must strike a balance: providing auditable, secure custody without introducing a single point of failure.
3. The fragmentation problem and the search for a standard
BTCFi remains fragmented at the asset layer. Unlike stablecoins, which have converged on widely accepted standards, wrapped BTC is split across multiple, chain-specific representations such as WBTC on Ethereum. This fragmentation dilutes liquidity, forces users to navigate inconsistent custody and risk profiles, and prevents cross-chain composability.
The lack of a universal standard stems from the unresolved trade-off between trust minimization and usability: centralized wrappers offer liquidity and operational simplicity but introduce custodial and censorship risk, while decentralized options align with Bitcoin’s ethos but struggle with adoption and integration.
The most probable near-term scenario is a handful of trusted wrappers optimized for distinct user segments. For BTCFi to scale, this unification is essential: the wrapped BTC that succeeds in becoming Bitcoin’s “USDC equivalent” will dominate the market for both institutional and retail participants.
🐯 More from Tiger Research
Read more reports related to this research.Disclaimer
This report has been prepared based on materials believed to be reliable. However, we do not expressly or impliedly warrant the accuracy, completeness, and suitability of the information. We disclaim any liability for any losses arising from the use of this report or its contents. The conclusions and recommendations in this report are based on information available at the time of preparation and are subject to change without notice. All projects, estimates, forecasts, objectives, opinions, and views expressed in this report are subject to change without notice and may differ from or be contrary to the opinions of others or other organizations.
This document is for informational purposes only and should not be considered legal, business, investment, or tax advice. Any references to securities or digital assets are for illustrative purposes only and do not constitute an investment recommendation or an offer to provide investment advisory services. This material is not directed at investors or potential investors.
Terms of Usage
Tiger Research allows the fair use of its reports. ‘Fair use’ is a principle that broadly permits the use of specific content for public interest purposes, as long as it doesn't harm the commercial value of the material. If the use aligns with the purpose of fair use, the reports can be utilized without prior permission. However, when citing Tiger Research's reports, it is mandatory to 1) clearly state 'Tiger Research' as the source, 2) include the Tiger Research logo. If the material is to be restructured and published, separate negotiations are required. Unauthorized use of the reports may result in legal action.