Web3 Paradox: How Transparency Builds and Breaks Trust
In a world where everyone watches, even good actors bleed
This report was written by Tiger Research, analyzing how blockchain transparency serves as both a strength and vulnerability in Web3 ecosystems, exposing misconduct while creating new attack vectors for projects and large holders.
TL;DR
Blockchain transparency has enabled communities to uncover misconduct and redistribute power, but it has also introduced new vulnerabilities. Visibility now serves as both an asset and a liability for Web3 projects, creating pathways for strategic attacks and crowd-driven volatility.
While transparency amplifies systemic risks — including insider exposure and protocol exploitation — retreating from it would compromise Web3’s foundational principles of open verification and decentralized trust.
Long-term success in Web3 will not be achieved by concealing activity, but by building systems resilient enough to operate and thrive under continuous public scrutiny.
1. Transparency’s New Risk: From Monitoring to Attacking
Blockchain transparency has become a core value in the Web3 industry. Unlike centralized databases, where a single entity controls data access, blockchain operates on a transparent and immutable ledger that all participants can verify in real time. Transparency is now a foundational element of Web3.
Thanks to this transparency, Web3 users can now monitor the activities of projects they follow in real time. They can track the wallet activities of founders, investors, and large holders, identifying suspicious token movements within minutes. In the Web2 environment, insider activities often remained hidden behind private bank accounts, inaccessible to the public. In contrast, Web3’s radical transparency exposes all transactions immediately. Compared to traditional finance, where such disclosures can take months, the real-time visibility of blockchain represents a transformative shift.
However, this transformation has introduced a structural paradox. Transparency, originally intended to enhance accountability and enable user oversight, is increasingly being weaponized to attack projects and large holders, even when there is no evidence of unethical behavior.
This report explores both the positive and negative effects of blockchain transparency and poses a critical question: Should Web3 continue to pursue absolute transparency at all costs?
2. The Double-Edged Effects of Transparency
2.1. Positive Side: Exposing Insider Behavior and Restoring Market Fairness
Across 2024 and 2025, a series of insider monitoring efforts uncovered projects where team wallets, influencers, and early backers appeared to have engaged in token sales. These insider activities were immediately exposed through blockchain transparency, triggering a strong backlash from the community.
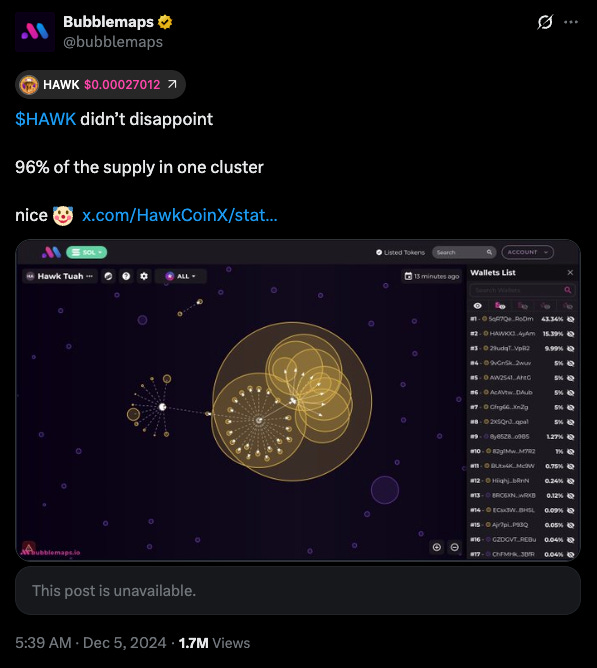
For example, in the case of HAWK Memecoin, over 96% of the token supply was found to be concentrated among the project team and its affiliates. Once this information surfaced, the market response was severe: the token's market capitalization fell sharply from a peak of $500 million to below $60 million, drawing regulatory scrutiny and undermining its credibility.
Blockchain transparency has enabled communities to act as real-time enforcers. Whether led by influencers or anonymous founders, project teams that failed to engage transparently often faced accusations of manipulation, even when their actions technically complied with legal requirements.
Although transaction data is publicly visible to all participants, interpreting its significance remains a complex task. Accurately understanding the intent and context behind each transaction requires specialized expertise, making it difficult for general users to fully interpret the information. However, with the advancement of sophisticated on-chain analytics tools, this gap is gradually narrowing. Users are now increasingly able to extract actionable insights from complex transaction flows and apply them to their decision-making processes.
2.2. Negative Side: When Transparency Backfires on the Platforms Themselves
Today, advanced on-chain analytics tools allow participants to access and interpret blockchain data with increasing ease. However, this increased visibility also introduces new risks. As monitoring capabilities expand through on-chain analytics, transparency itself can be weaponized. Projects—particularly those with weak governance structures or highly concentrated token distributions—face heightened risks of manipulation and coordinated exploitation.
On March 26, 2025, Hyperliquid encountered a novel form of protocol-level risk, one enabled by the very transparency it promotes. Based on Arkham's analysis, the event unfolded as follows:
The attacker analyzed Hyperliquid’s public liquidation thresholds and HLP vault size to calculate a precise liquidation point.
Using three wallets, the attacker opened a $4.1M short position and two long positions ($2.15M and $1.9M) to artificially push up JELLY’s price.
As JELLY’s price rose, the first short position was liquidated, and losses were passed to the HLP vault.
External traders joined long positions, driven by OKX listing rumors and expectations of a short squeeze, intensifying price volatility.
Hyperliquid intervened by forcefully delisting JELLY and closing all open positions at $0.0095 to contain systemic risk.
Hyperliquid’s architecture, which publicly displays vault exposure, margin levels, liquidation thresholds, and open positions, inadvertently enabled attackers to apply precise pressure. In this case, transparency, rather than deterring manipulation, facilitated a coordinated financial attack in real time.
Ironically, the transparency that Hyperliquid promoted contributed both to financial losses and to broader concerns about the platform’s governance and resilience. To prevent further systemic damage, the team was ultimately forced to delist JELLY — an action that, while necessary, stood in contrast to decentralization principles.
Similar risks may arise in other projects. Even with sound technical design, transparent protocols remain susceptible to unexpected attacks. Without complementary defense mechanisms and clear response frameworks, transparency, while intended to build credibility, can instead become a source of systemic instability. In this context, transparency is not only a strength; it is also a strategic vulnerability.
2.3. Neutral Side: When Transparency Becomes a Tool for Crowd Strategy
The outcomes of transparency cannot be simply classified as positive or negative. In certain situations, transparency functions as a tool with blurred boundaries between promoting market integrity and enabling individual self-interest.
This emerging trend was clearly illustrated on Hyperliquid, where some investors began targeting large traders based solely on their visible positions. A notable case involved a trader known as CBB, who publicly called for a coordinated effort to liquidate a whale, claiming that eight-figure capital was already mobilized. Importantly, the targeted trader had not violated any protocol or engaged in misconduct; the sheer size of their position made them an inevitable target.
Furthermore, this behavior reflects a psychological pattern within Web3, a modern iteration of the "David versus Goliath" mentality. In traditional narratives, David is portrayed as the righteous underdog, while Goliath, despite being simply a strong and capable soldier fighting the same war, is cast as the adversary solely because of his strength. Similarly, in Web3 environments, large holders often become symbolic targets, regardless of their intent or actions. Visibility magnifies perception, and perception, rather than facts, increasingly shapes collective behavior.
Innocent investors may suffer reputational harm or financial losses for simply being visible. The fear of public targeting may discourage large-scale capital from entering the ecosystem, ultimately limiting growth opportunities for new projects. At the same time, organized crowd behavior can consolidate power among influential groups — ironically creating new forms of centralization within systems originally designed to be decentralized.
3. The New Reality: Should Projects Be More Transparent?
Transparency in Web3 is a double-edged sword. On the positive side, it enables communities to uncover insider misconduct and redistribute market power through collective action. On the negative side, it exposes projects to unexpected attacks, including strategic market manipulation. While transparency is intended to build trust, it can also become a catalyst for systemic instability.
Yet despite these risks, abandoning transparency is neither feasible nor desirable for most Web3 projects. Transparency is fundamental to the ethos of Web3: it enables open verification, reduces information asymmetries, and shifts trust from centralized intermediaries to decentralized systems. Without it, the core principles that differentiate Web3 from traditional financial and technological structures would erode.
Rather than retreating from transparency, projects must evolve their strategies to coexist with it. This includes embedding resilience into protocol design, developing clear crisis-management frameworks, and proactively managing perception and communication with their communities.
For example, some projects are establishing DAO-based emergency procedures to ensure that interventions are governed by transparent and community-approved frameworks. Others regularly conduct bug bounty programs to identify protocol weaknesses before they can be exploited.
Transparency in Web3 cannot be reduced; it is a structural inevitability. Projects must recognize that transparency will continue to amplify both opportunity and risk. Those who succeed will not be the ones who hide better, but the ones who build systems strong enough to withstand being seen.
🐯 More from Tiger Research
Read more reports related to this research.Disclaimer
This report has been prepared based on materials believed to be reliable. However, we do not expressly or impliedly warrant the accuracy, completeness, and suitability of the information. We disclaim any liability for any losses arising from the use of this report or its contents. The conclusions and recommendations in this report are based on information available at the time of preparation and are subject to change without notice. All projects, estimates, forecasts, objectives, opinions, and views expressed in this report are subject to change without notice and may differ from or be contrary to the opinions of others or other organizations.
This document is for informational purposes only and should not be considered legal, business, investment, or tax advice. Any references to securities or digital assets are for illustrative purposes only and do not constitute an investment recommendation or an offer to provide investment advisory services. This material is not directed at investors or potential investors.
Terms of Usage
Tiger Research allows the fair use of its reports. ‘Fair use’ is a principle that broadly permits the use of specific content for public interest purposes, as long as it doesn't harm the commercial value of the material. If the use aligns with the purpose of fair use, the reports can be utilized without prior permission. However, when citing Tiger Research's reports, it is mandatory to 1) clearly state 'Tiger Research' as the source, 2) include the Tiger Research logo. If the material is to be restructured and published, separate negotiations are required. Unauthorized use of the reports may result in legal action.