An AI-powered, automation-driven era is approaching. For automation to become truly autonomous, it must incorporate native payment capabilities. The market is already positioning for this shift.
Key Takeaways
The payer is shifting from humans to AI agents, making payment infrastructure a central requirement for true autonomy
Big Tech, including Google AP2 and OpenAI Delegated Payment, is designing approval-based automated payment systems on top of existing platform infrastructure
Crypto, through ERC-8004 and x402, enables intermediary-free payment models using NFT-based identity and smart contracts
Big Tech prioritizes convenience and consumer protection, while crypto emphasizes user sovereignty and broader agent-level execution
The key question ahead is whether payments will be controlled by platforms or executed by open protocols
1. Payments Are No Longer Exclusive to Humans
Recently, “OpenClaw” drew attention. Unlike AI systems such as ChatGPT or Gemini that primarily retrieve and organize information, OpenClaw enables AI agents to execute tasks directly on a user’s local PC or server.
Through messaging platforms such as WhatsApp, Telegram, and Slack, users can issue commands, and the agent autonomously performs tasks including email management, calendar coordination, and web browsing.
Because it operates as open-source software and is not tied to a specific platform, OpenClaw functions more like a personal AI assistant. This architecture has attracted interest for its flexibility and user-level control.
However, a critical limitation remains. For AI agents to operate with full autonomy, they must be able to execute payments. At present, agents can search for products, compare options, and add items to a cart, but final payment authorization still requires human approval.
Historically, payment systems have been designed around human actors. In an AI agent–driven environment, this assumption no longer holds. If automation is to become fully autonomous, agents must be able to assess, authorize, and complete transactions independently within defined constraints.
In anticipation of this shift, both major technology firms and crypto-native projects have introduced technical frameworks over the past year aimed at enabling agent-level payments.
2. Big Tech: Agent Payments Built on Existing Infrastructure
In January 2025, Google introduced AP2, Agent Payment Protocol 2.0, expanding its AI agent payment infrastructure. While OpenAI and Amazon have outlined related initiatives, Google is currently the only major firm with a structured implementation framework.
AP2 separates the transaction process into three mandate layers. This structure allows each stage to be monitored and audited independently.
Intent Mandate: Records what the user wants to do
Cart Mandate: Defines how the purchase should be executed under preset rules
Payment Mandate: Executes the actual transfer of funds
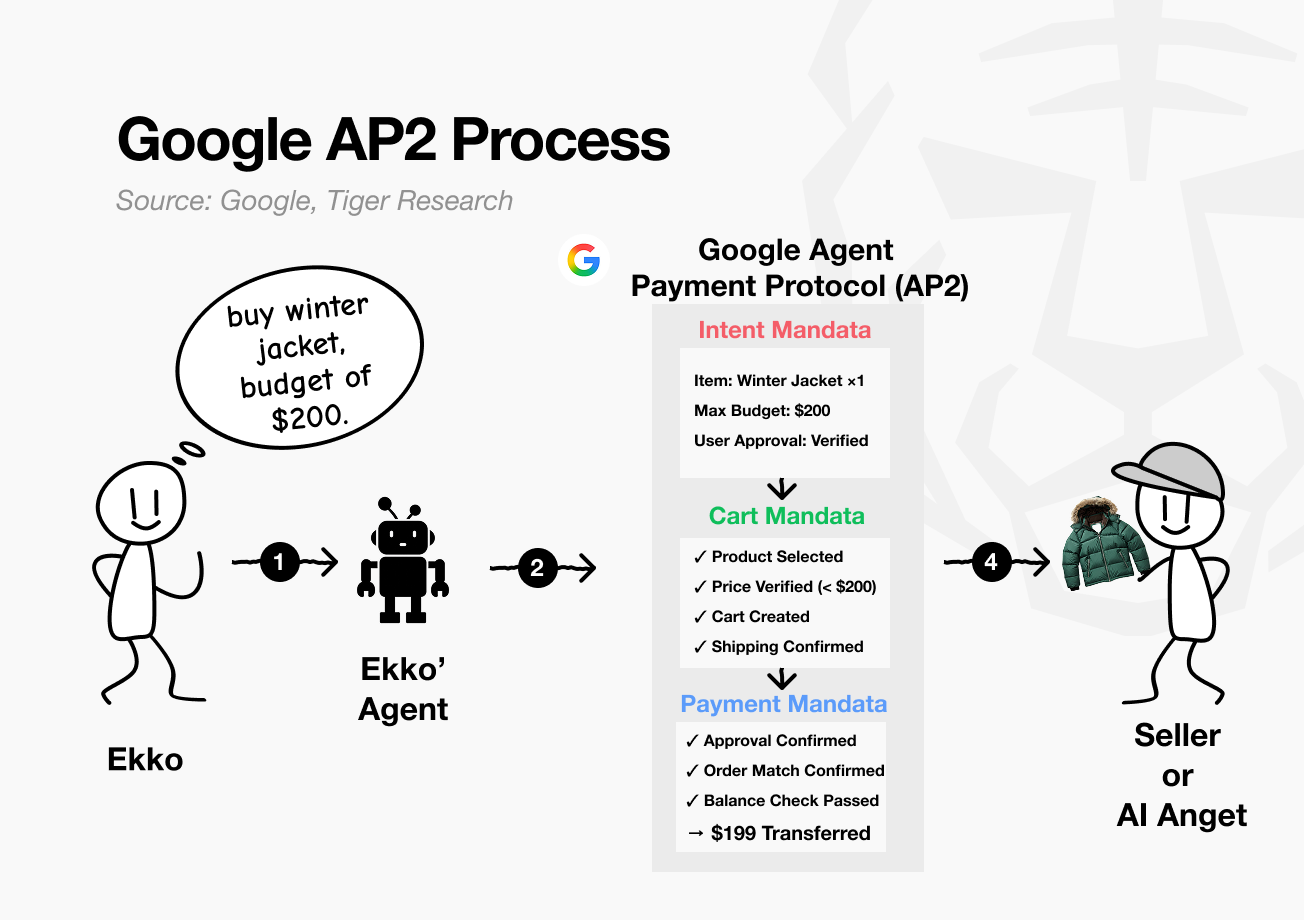
Assume Ekko asks an AI agent on Google Shopping to “find and purchase a winter jacket under $200.”
Intent Mandate: Ekko instructs the AI agent to purchase “one winter jacket with a maximum budget of $200.”
This information is recorded on-chain as a digital contract, referred to as the Intent Mandate.
Cart Mandate: The AI agent follows the stated intent, searches partner merchants for products that match “one winter jacket” and “maximum budget of $200,” and adds a qualifying item to the cart.
“Item selected: Winter jacket”, “Price verified: $199 (within budget ✓)”
“Added to cart”, “Shipping address confirmed.”
Payment Mandate: Ekko reviews the item selected by the AI agent and clicks the payment approval button. The $199 is processed through Google Pay. Alternatively, the AI agent may complete the payment automatically within predefined parameters.
Throughout this process, the user does not need to input additional information. In the case of Google AP2, the system operates on top of Google Pay and utilizes pre-registered card details and shipping addresses. Because AP2 relies on existing user credentials, it reduces onboarding friction and simplifies adoption.
However, Google currently supports agent-based payments only for companies within its partner network. As a result, usage remains confined to a controlled ecosystem, limiting broader interoperability and open access.
3. Crypto: Self-Custody and Open Exchange
Crypto is also developing payment infrastructure for AI agents, but the approach differs from that of Big Tech. While large platforms build trust within controlled ecosystems, crypto begins with a different question: can AI agents be trusted without relying on a central platform?
Two core standards aim to address this objective: Ethereum’s ERC-8004 and Coinbase’s x402.
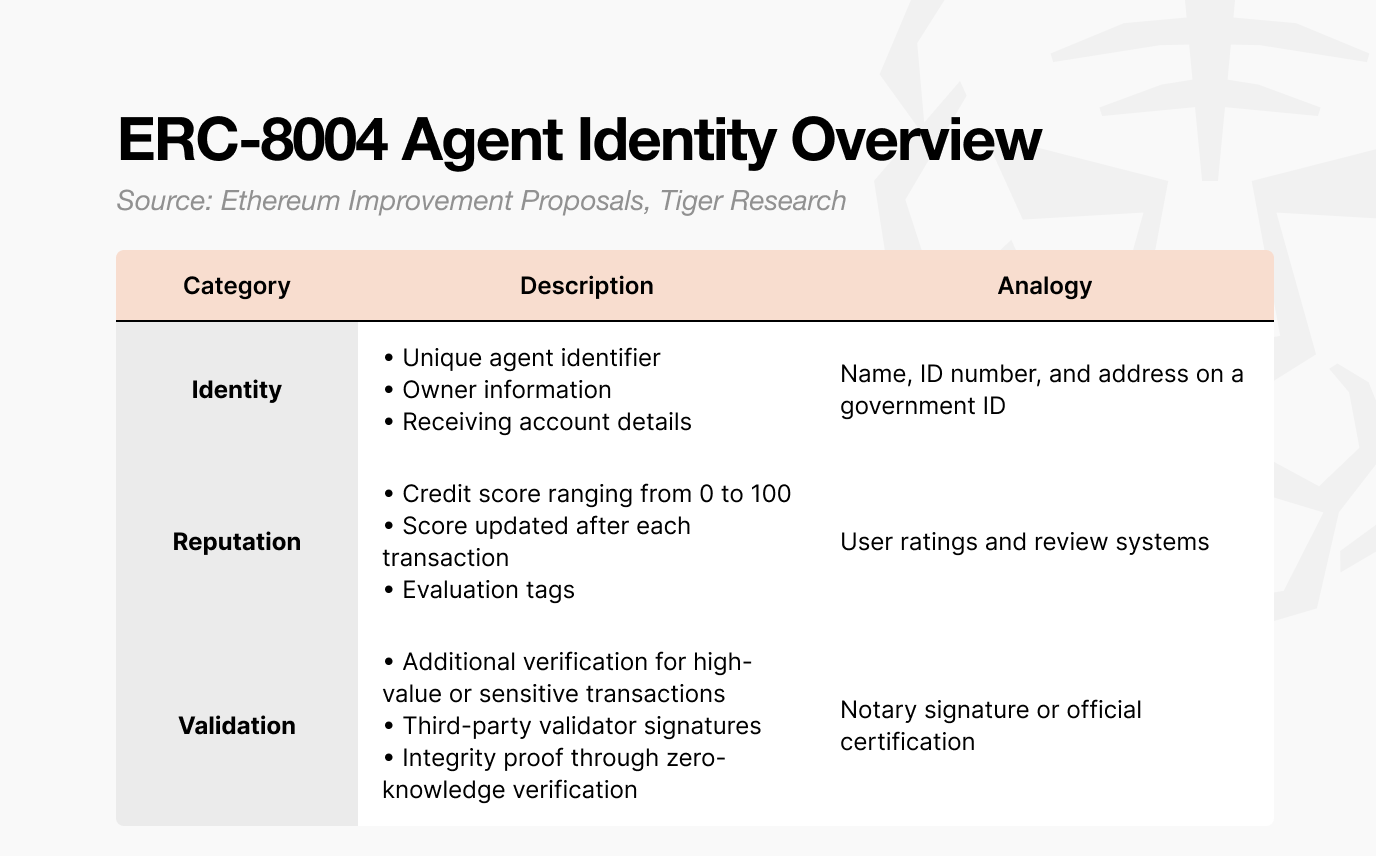
First, consider the identity layer. Just as users require an ID to access digital services, AI agents operating on blockchain networks must also be identifiable. ERC-8004 serves this function.
It is issued as an NFT, not as a media-based collectible. Instead, it is a credential NFT that contains structured identity data. Each token includes three components:
Identity
Reputation
Validation
Together, these elements function as a verifiable on-chain identity certificate.
In online commerce, participants review ratings and transaction history before engaging with a counterparty. The same logic applies to AI agents. ERC-8004 provides agents with verifiable credentials, allowing other agents to assess whether a transaction is appropriate based on transparent data.
However, identity alone does not enable value transfer. A payment mechanism is required for funds to move. That role is fulfilled by x402.
If ERC-8004 functions as a digital identity card, x402 operates as the payment rail. Developed by Coinbase, x402 is a crypto-native payment standard for AI agents. It enables agents to transact autonomously in stablecoins.
Its core feature is automated smart contract execution. Conditional logic such as automatic transfer upon fulfillment of predefined criteria is embedded directly in code. Once conditions are met, settlement occurs without human intervention.
When ERC-8004 for identity and x402 for payment are combined, AI agents can verify counterparties and execute transactions without relying on a central platform. Trust and settlement are handled at the protocol level rather than through platform control.
Assume a near-future AI agent environment.
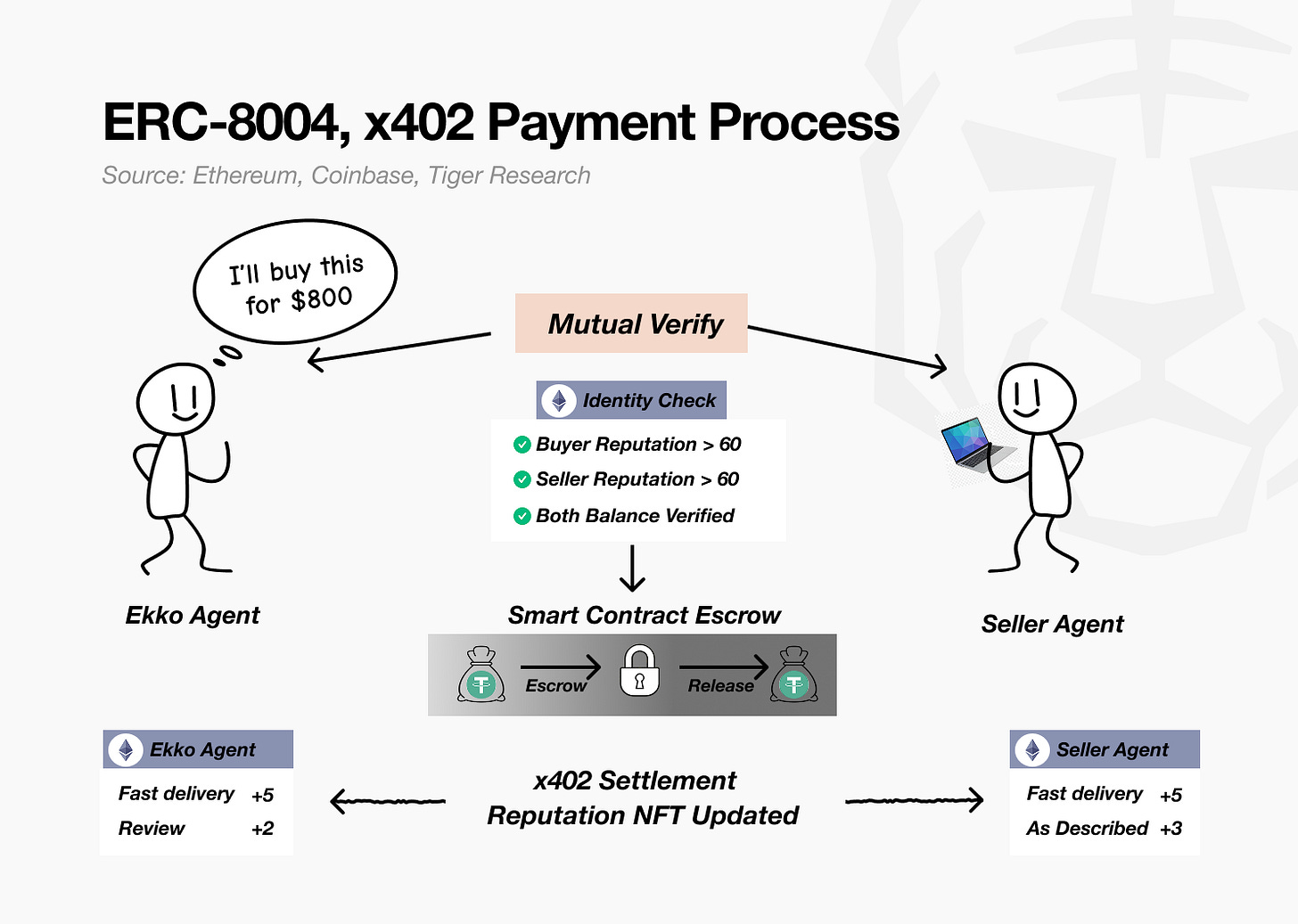
Ekko instructs his AI agent (Agent A) to purchase a used laptop with a maximum budget of $800. The marketplace operates its own AI agent (Agent B), which communicates directly with Ekko’s agent to execute the transaction.
Mutual Verification
Before the transaction, both agents verify each other’s credentials and confirm that the product meets the specified requirements.
* Identity Check: Verification via ERC-8004 NFT
* Ekko’s agent: Reputation score 72, $800 balance confirmed
* Seller’s agent: Reputation score 70, qualifying laptop inventory confirmed
→ Result: Both agents approved for the transactionSmart Contract Escrow
Once verification is complete, the transaction proceeds. Each agent interacts through the x402 protocol to transfer and confirm funds.
* Escrow: $800 is transferred from Ekko’s agent wallet to a smart contract
* Conditional Hold: Funds remain locked until delivery confirmation
→ Release: Upon confirmation of delivery, $800 is automatically transferred to the sellerSettlement and Reputation Update(x402 Settlement & Reputation NFT Updated)
After settlement, both agents’ reputation records are updated.
* Ekko’s agent: Reputation 72 → 80 (+5 Fast delivery, +3 As described)
* Seller’s agent: Reputation 70 → 78 (+5 Fast delivery, +3 As described)
→ The updated evaluation records are written to each agent’s ERC-8004 NFT
Throughout this process, no intermediary is involved. No platform approval is required. The two AI agents transact directly through blockchain-based verification and settlement. This reflects the crypto-native model for agent-to-agent commerce.
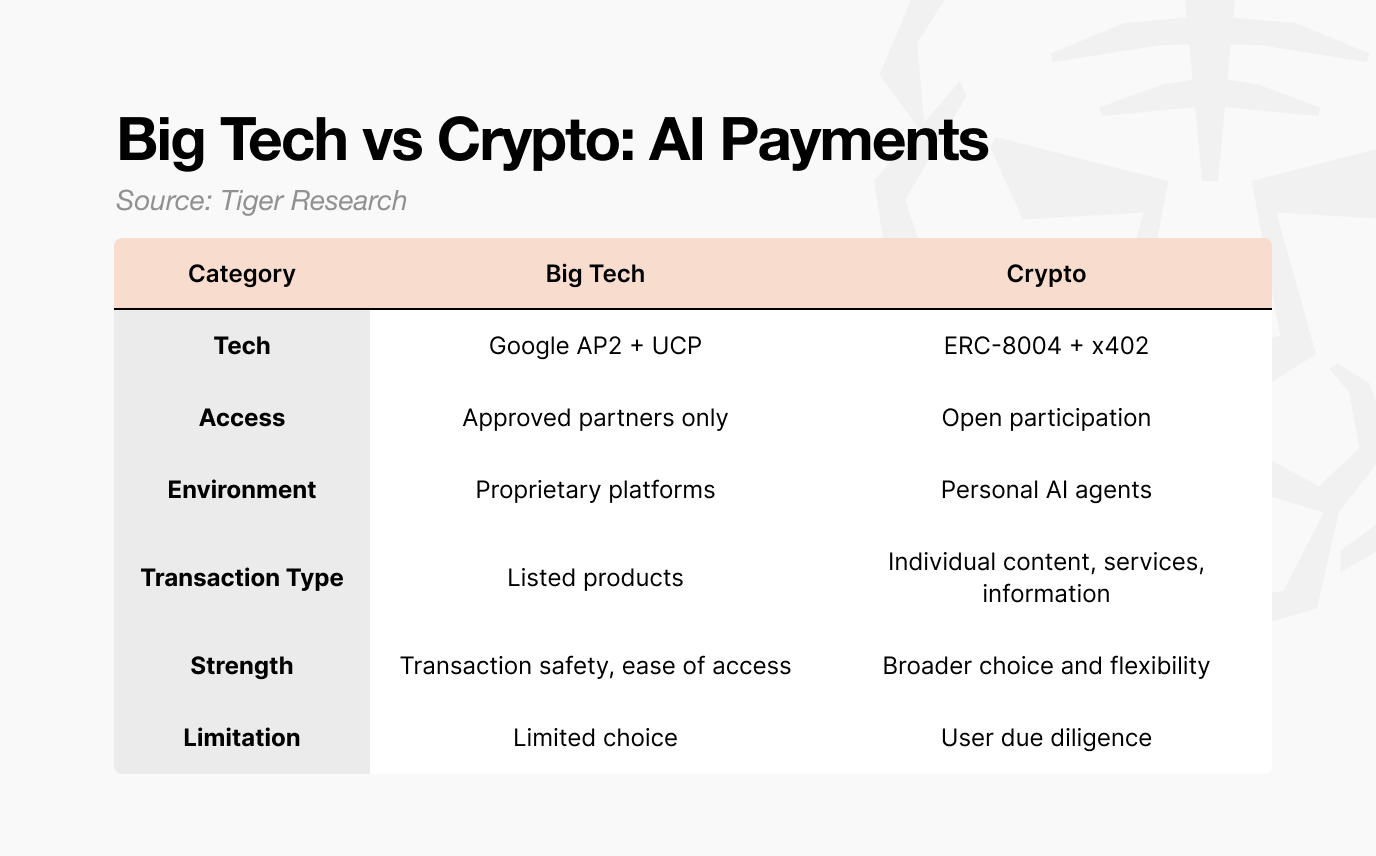
4. Big Tech vs Crypto: Diverging Operational Domains for AI Agents
Google AP2 represents a controlled model designed for approved partners.
Google limits marketplace participation to vetted merchants, citing consumer protection. Even with a structured mandate framework, agent behavior cannot be fully guaranteed. Unlike deterministic systems where input and output are directly matched, AI agent execution introduces probabilistic outcomes.
If an agent connects to an unreliable partner and a transaction error occurs, liability may ultimately fall on the payment infrastructure provider. To reduce even a marginal failure probability, such as 0.01 percent, Google has an incentive to narrow its ecosystem.
A restricted ecosystem improves stability and oversight. However, it may also limit the agent’s ability to operate autonomously across broader markets and optimize across a wide range of options.
In contrast, ERC-8004 and x402 reflect a more open architecture. The crypto model is designed to be permissionless and interoperable rather than platform-bound.
AI agents remain in an early stage of development. End-to-end execution, from complex request to autonomous payment, is not yet seamless.
However, the anticipated long-term scenario involves agents independently managing routine consumption. For example, a user may instruct an agent to restock groceries, and the agent would assess inventory gaps and complete purchases automatically.
Large platforms may attempt to aggregate major retail channels to support this model within a unified environment. This approach could enable reliable, everyday use cases within a controlled framework.
However, integrating all potential counterparties, including small online merchants, independent websites, decentralized finance protocols, and trading venues, presents structural limits for a closed ecosystem.
In addition, if digital content increasingly shifts toward paid access models, agents may need to execute high-frequency microtransactions.
Open crypto standards may offer structural advantages. For example, an AI agent could purchase 1,000 creator-generated images at $0.01 per unit or pay $1 to access a research article. For small-denomination, programmable payments, crypto-native rails may offer operational efficiency.
That said, the absence of a central authority introduces trade-offs. Identity evaluation standards must be established in a decentralized manner, and no single entity bears ultimate responsibility for failure. Balancing openness with accountability remains a key design challenge that will depend on both technical maturity and usability improvements.
In summary, both Big Tech and crypto pursue the same objective: enabling autonomous AI agent commerce. The distinction lies in architecture. Big Tech favors closed, controlled systems, while crypto advances open, protocol-based models.
Rather than a zero-sum outcome, the more plausible trajectory is interoperability between the two approaches. Continued development must prioritize reliability and user experience at the current stage of technical progress.
🐯 More from Tiger Research
Read more reports related to this research.Disclaimer
This report has been prepared based on materials believed to be reliable. However, we do not expressly or impliedly warrant the accuracy, completeness, and suitability of the information. We disclaim any liability for any losses arising from the use of this report or its contents. The conclusions and recommendations in this report are based on information available at the time of preparation and are subject to change without notice. All projects, estimates, forecasts, objectives, opinions, and views expressed in this report are subject to change without notice and may differ from or be contrary to the opinions of others or other organizations.
This document is for informational purposes only and should not be considered legal, business, investment, or tax advice. Any references to securities or digital assets are for illustrative purposes only and do not constitute an investment recommendation or an offer to provide investment advisory services. This material is not directed at investors or potential investors.
Terms of Usage
Tiger Research allows the fair use of its reports. ‘Fair use’ is a principle that broadly permits the use of specific content for public interest purposes, as long as it doesn’t harm the commercial value of the material. If the use aligns with the purpose of fair use, the reports can be utilized without prior permission. However, when citing Tiger Research’s reports, it is mandatory to 1) clearly state ‘Tiger Research’ as the source, 2) include the Tiger Research logo. If the material is to be restructured and published, separate negotiations are required. Unauthorized use of the reports may result in legal action.